921 password attacks happen every second.
Is your company at risk?
Quickly find out with an External Exposure Scan.
Complimentary | Results in 72 hours | Real-life findings | Risk prioritization | Tailored & actionable results
External threats move fast. Move faster with visibility into your external surface.
Stolen credentials were the leading cyberattack vector in 2022, with an average cost of $4.5M. If you have employees, your corporate logins are up for grabs.
It’s time to intercept leaked emails, stolen login cookies and exposed API keys. With CybelAngel’s Account Takeover Prevention, you can detect them before they lead to a million-dollar breach. Let us do a complimentary scan for you to see if your company is at risk.
Complete. Submit. Within 72 business hours, we'll show you up to three exposures that may be putting your company at risk.
Let’s go!
“CybelAngel is best of breed for [detecting] leaked data that can be accessed outside the enterprise perimeter, such as public cloud environments or connected storage devices.”
COMPETITIVE LANDSCAPE: Digital risk protection services 2021, Elizabeth Kim, Ruggero Contu | GARTNER
Visibility into vulnerable
blind spots
We provide the most comprehensive, in-depth, ever-expanding scanning surface on the market.
Critical insights
into critical threats
We send only actionable alerts with zero false positives so you can focus on what matters most.

Lightning-fast
threat detection
Proactively identify and resolve threats with lightning-fast detection well before they’re exploited.
Activate the full scope of CybelAngel for 3 days and detect exposure through:
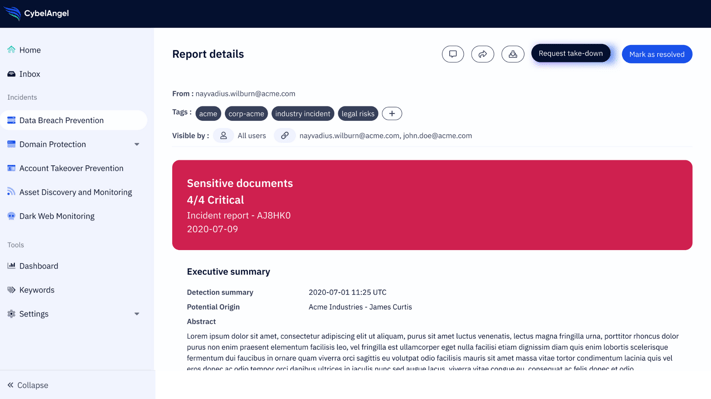
Data Breach Prevention
Asset Discovery & Monitoring
Account Takeover Prevention
Domain Protection
Dark Web Monitoring
We will scan a range of sources including:
- File servers
- Databases
- Cloud storage
- Websites
- SaaS Applications
- Code sharing tools
- Domain names
- Deep and dark web
- Shadow IT
- IOT

